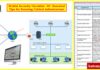
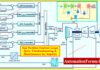
- Instrumentation
- Automation
- Procedures
- Pressure Calibration
- Flow Calibration
- Level Calibration
- Temperature Calibration
- Signal Convertors Calibration
- Displacement measurement Calibration
- Control Valve Calibration
- Analytical Instruments Calibration
- Weighing system Calibration
- Different types of Calibrators
- Calibration Guidelines
- Calibration Templates
- Preventive Maintanance Procedure
- Troubleshooting Procedure
- Maintenance checklist
- Calculators
- EPC Docs
- Interview Q&A
- More
- Instrumentation
- Automation
- Procedures
- Pressure Calibration
- Flow Calibration
- Level Calibration
- Temperature Calibration
- Signal Convertors Calibration
- Displacement measurement Calibration
- Control Valve Calibration
- Analytical Instruments Calibration
- Weighing system Calibration
- Different types of Calibrators
- Calibration Guidelines
- Calibration Templates
- Preventive Maintanance Procedure
- Troubleshooting Procedure
- Maintenance checklist
- Calculators
- EPC Docs
- Interview Q&A
- More
©