- What is meant by Cyber attack & what are its types?
- Types of cyberattacks
- 1. Denial-of-Service Attack
- 2. Direct-access Attack
- 3. Eavesdropping
- 4. Spoofing
- 5.Tampering
- 6.Repudiation Attack
- 7. Information Disclosure
- 8. Privilege Escalation Attack
- 9. Exploits
- 10. Social engineering
- 11. Indirect attack
- 12. Computer crime
- 13. Malware
- 14. Bots
- 15. Ransomware
- 16. Scareware
- 17. Phishing
- 18. Identity Theft
- 19. Intellectual Property Theft
- 20.Password Attacks
- 21. Bluesnarfing/ Bluejacking
- 22. DDoS
- 23. Keylogger
- List some common types of cyber attacks?
- Why is it called cyber?
- How Cyber attack can be overcome?
- What are the top 5 techniques to defend oneself against online attacks?
- Can you recover back from a cyberattack?
What is meant by Cyber attack & what are its types?
- A cyber attack is a harmful attack on your computer systems that comes from an unidentified source.
- A cyber assault enables unauthorized use of your digital device while acquiring access to or control of it.
- The term “cyber attack” refers to a variety of offensive strategies used to illegally gain control or access to a target system, which can be a website, computer system, a single digital device, or the entire network.
- These strategies pose a serious threat to computer systems, information stored therein, financial structures, and the network itself.
- Cyber attack aim to compromise the confidentiality of the data stored on the digital device and its integrity.
Types of cyberattacks
1. Denial-of-Service Attack
A denial-of-service attack, also known as a DOS attack, involves impacting the host device that is connected to the internet in order to fully shut down the network with worthless data. Websites or services housed on the servers of banks and credit card payment gateways are the target of a DOS attack.
2. Direct-access Attack
Getting physical access to a computer or a component of it allows one to execute numerous tasks or install various kinds of security-compromising devices. Using portable devices, the attacker can download crucial information or install software that has been worm-infected.
3. Eavesdropping
As the term implies, eavesdropping refers to covertly listening in on a network’s hosts’ conversations. There are numerous tools available for eavesdropping, including Carnivore and Narus Insight.
4. Spoofing
5.Tampering
6.Repudiation Attack
A repudiation attack takes place when the user disputes having carried out a certain activity or having started a transaction. A user can simply claim that they were unaware of the transaction or communication and that it never happened in the future.
7. Information Disclosure
An information disclosure breach occurs when information that was supposed to be safe is made available to dishonest or unreliable parties.
8. Privilege Escalation Attack
A privilege escalation attack is a kind of network intrusion that gives a user elevated access to the network that was previously not permitted. By taking advantage of the programming flaws, the attacker gives the network higher access.
9. Exploits
A software program created to exploit a system weakness constitutes an exploit assault. The attacker intends to acquire quick access to a computer system and take over, either by enabling privilege escalation or by launching a denial-of-service assault.
10. Social engineering
11. Indirect attack
An indirect attack is one that originates from a computer belonging to a third party because it is getting harder to determine where the assault originated.
12. Computer crime
A computer crime is a crime that is carried out via a network and a computer.
13. Malware
14. Bots
A software program called a bot performs simple, repetitive activities automatically. Whether malevolent or not, bots are frequently observed starting a DoS attack or click fraud when browsing the internet.
15. Ransomware
A ransomware attack is a form of cyber security risk that initially blocks access to your computer system and then demands payment to remove the restriction. Only online payment methods are accepted for this ransom, after which the user will be given access to their system.
16. Scareware
Scareware is a threat that poses as a legitimate system notification and directs you to download and buy possibly harmful and worthless software.These scareware pop-ups appear to be like any other system alerts but aren’t. The fundamental goal of scareware is to install fear in consumers and utilize that fear to persuade them to download pointless software.
17. Phishing
Phishing is a cyberthreat that tries to acquire private data such as passwords, usernames, and other specifics for nefarious purposes. In essence, it is an email scam in which the fraudster sends a message that appears to be authentic in an effort to obtain personal data
18. Identity Theft
When someone steals your personal information and uses it to perpetrate fraud, they are committing identity theft. When a thief impersonates others and uses their personal information for financial advantage, they have committed identity theft.
19. Intellectual Property Theft
When material protected by a copyright or a patent is stolen, it is considered intellectual property theft. Obtaining papers that contain commercial secrets, patents, or research is a felony committed online. An idea, a plan, and the process are being stolen.
20.Password Attacks
A password attack is a type of threat to the security of your system in which the assailant typically looks for ways to access your system password. To find the right password and get access to the system, they use an automated program.
21. Bluesnarfing/ Bluejacking
The threat of information being obtained illicitly is known as bluesnarfing. Using Bluetooth’s wireless and without the user’s knowledge, hackers can access the information and data on a Bluetooth-enabled phone.
Bluejacking is a simple form of marketing that involves transmitting texts, photos, or sounds to another Bluetooth-enabled device.
22. DDoS
A distributed denial of service is what DDoS essentially refers to. It is an attempt to temporarily disable any online service by creating a large amount of traffic from various sources or by suspending the operations of a server that is linked to the internet.
23. Keylogger
It is a type of spyware that may monitor activity on a computer system. Every keystroke made on the keyboard, websites visited, and all data available on the device can be recorded. The recorded log is subsequently forwarded to the designated recipient.
List some common types of cyber attacks?
- Malware
- DoS (denial-of-service) assaults
- Phishing and Spoofing
- Identity-Based Attacks
- Code Injection Attacks
- Supply Chain Attacks
Why is it called cyber?
- Originally, the word “cyber” was derived from the Greek adjective kubernetikos, which means “good at steering or piloting.”
- In French, it became “cybernetique”
- The cyber market is described as being of, involving, or related to computers or computer networks (such as the Internet).
How Cyber attack can be overcome?
One of the best ways to protect yourself from any cyber assault is to place your network behind a firewall. Firewall system that will stop brute force assaults on your network before they can cause any harm.
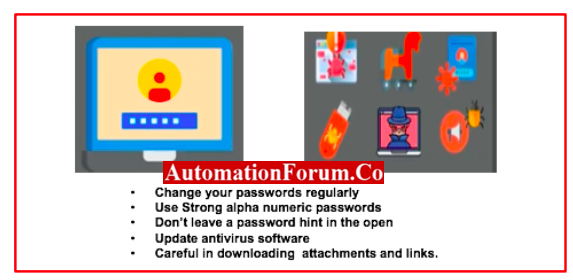
What are the top 5 techniques to defend oneself against online attacks?
Here are some actions you can take to safeguard yourself against online threats.
- Watch out for suspicious downloads, attachments, and links. Downloads, attachments, and links may include malware and ransomware.
- Always choose secure, lengthy passwords that are challenging to crack. Use separate passwords for each account that are unique, i.e. Passwords must contain capital letters, special characters, and at least 8 characters in length.
- Whenever possible, use multi-factor authentication. An additional layer of protection is added by multi-factor authentication.
- Use multi-factor authentication if it is available for the service you are using. Internet conversations should be secure.
- If you plan to access or provide any personal information, only use “HTTPS” sites. Useless websites should not be used.
- Regularly update your antivirus program. Ensure that regular updates are installed and that your anti-virus software is up to date.
- Send any unusual activity to your IT department.
Can you recover back from a cyberattack?
It is frequently possible to restore just enough essential services to enable continued operation, but it may take several months before everything are back to normal. In the meantime, we need strategy and necessary resources to manage and carry out operation.





